Prometheus Wept Log 3: New Feature - System Infiltration

Hi again! I hope you’re keeping safe and healthy. Previously, I’ve hinted at a big, unannounced feature of Prometheus Wept. Finally, enough progress has been made to talk about it. To begin, you may be aware that Prometheus Wept takes place in the aftermath of a cyber attack which corrupted most of our digital technology.
The new feature allows the protagonist to digitise their consciousness and enter corrupted computer networks as an avatar. This means that two turn-based battles can occur simultaneously and the actions taken in one battle can affect the other. Typically, this will involve your allies protecting the player character from physical enemies, while your avatar battles the network’s security protocols.
Each network is comprised of a number of nodes. Each node controls a system in the physical world, for example a door or defences. When an avatar defeats and captures a node, the player gains control of that system. To make more sense of this, here’s a concrete example which will be available in the upcoming demo.
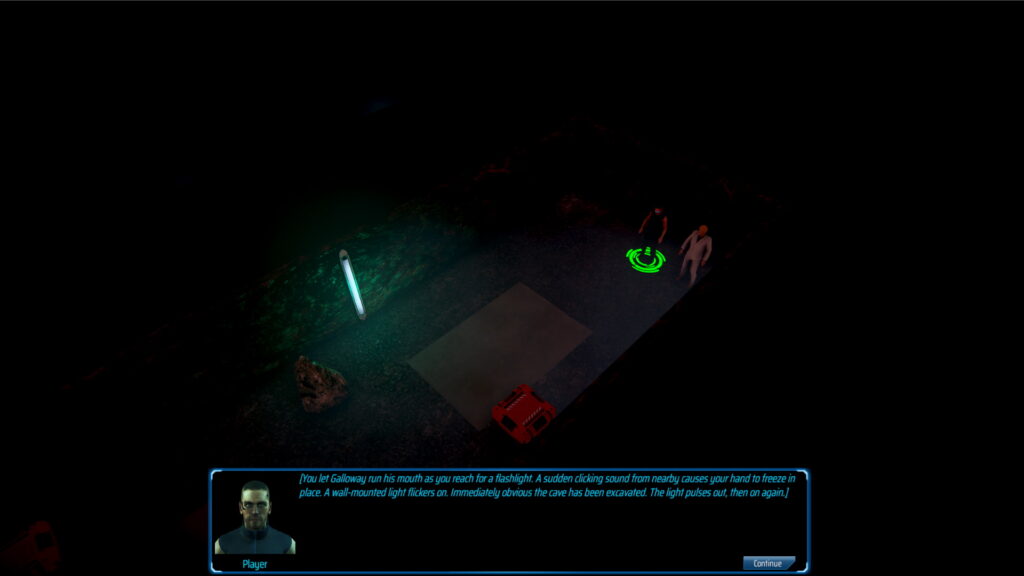

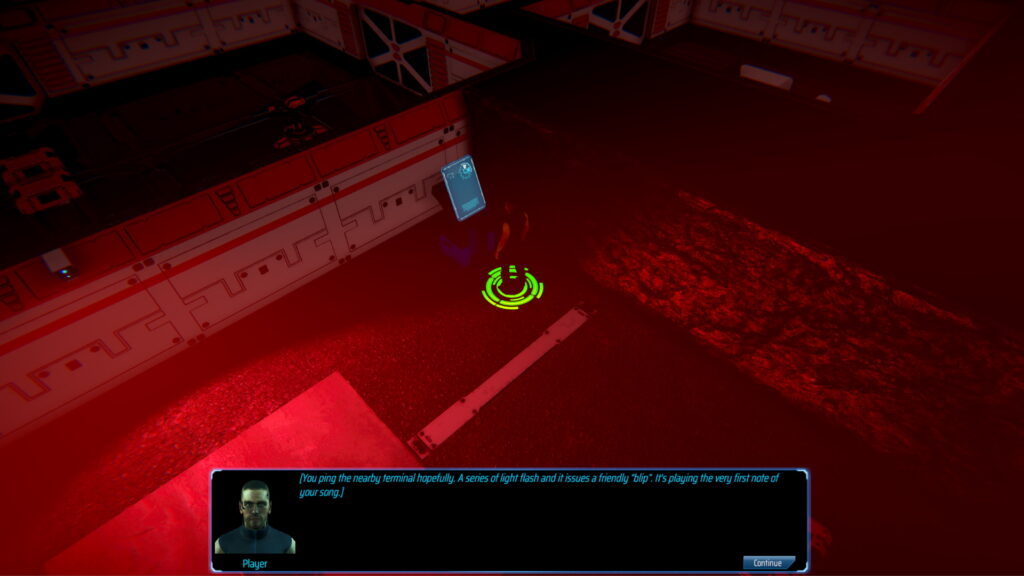
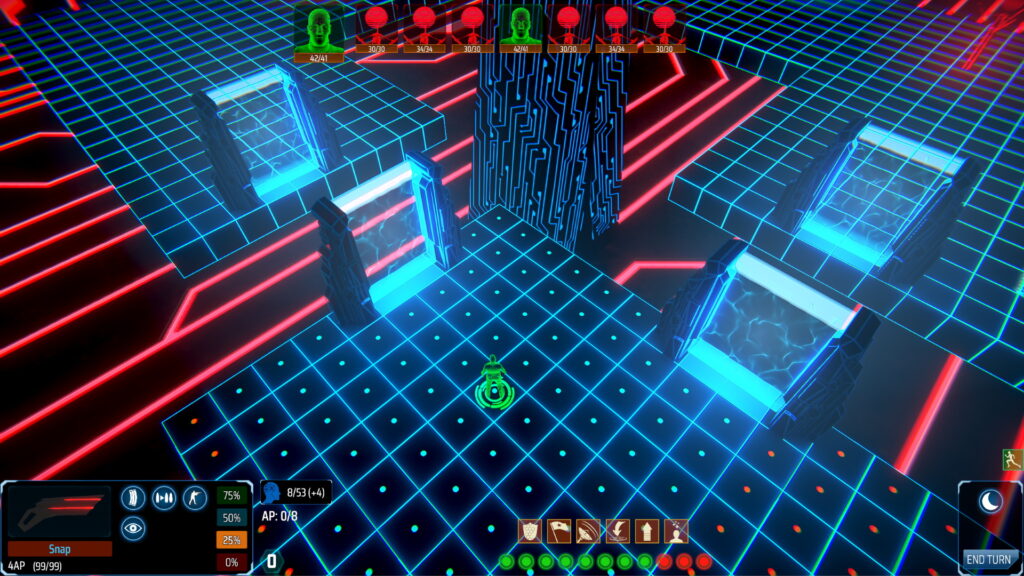
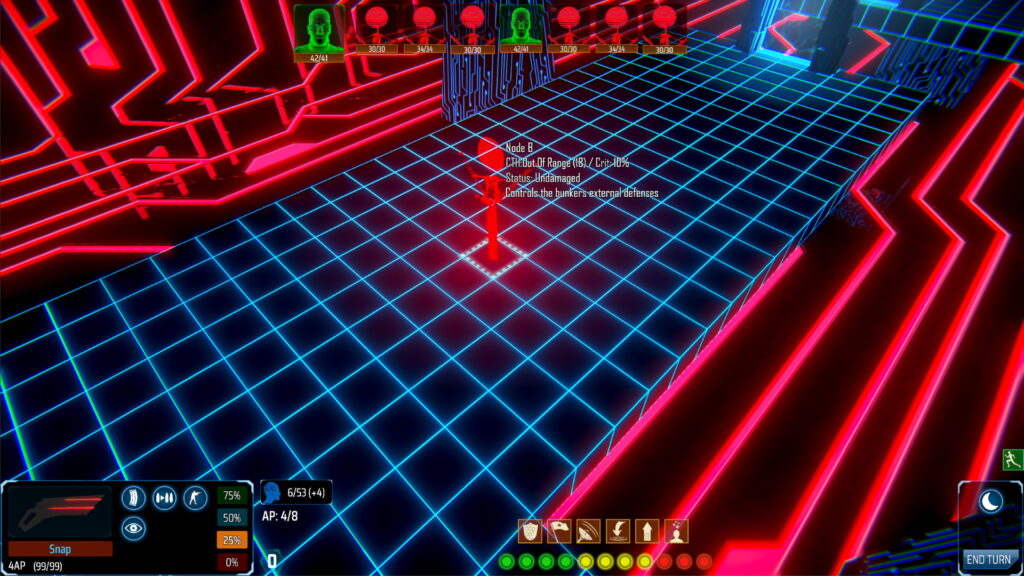
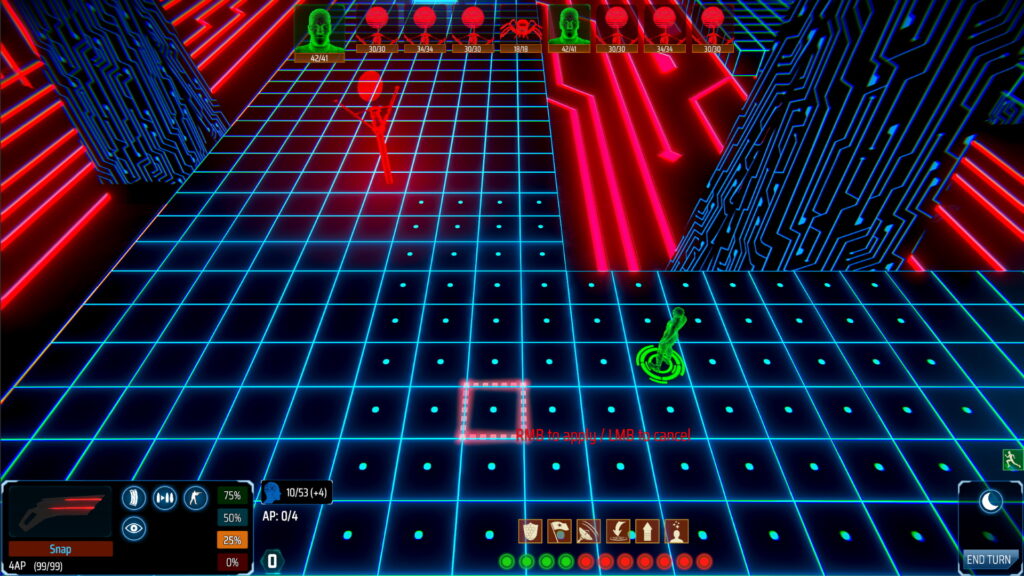
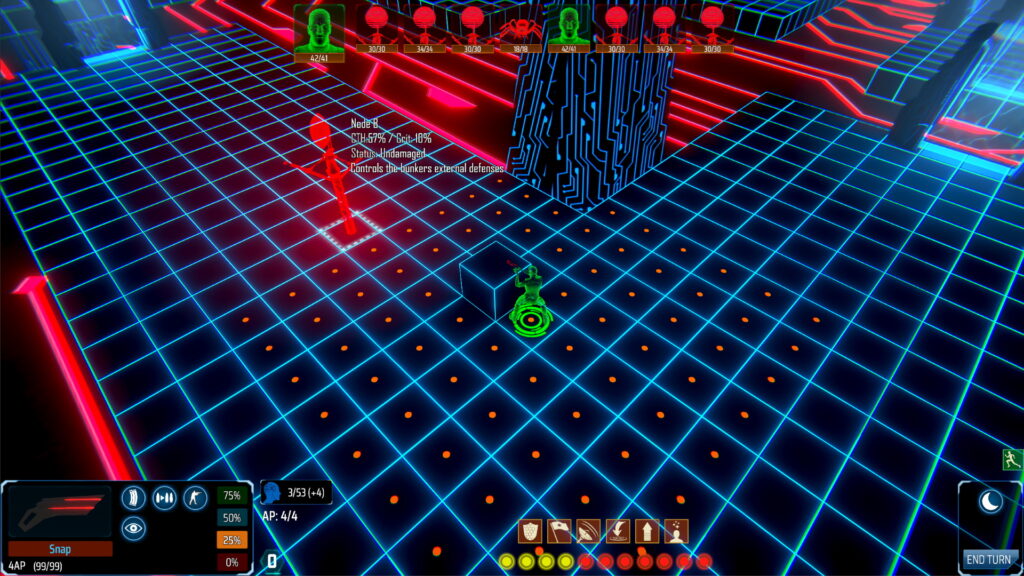
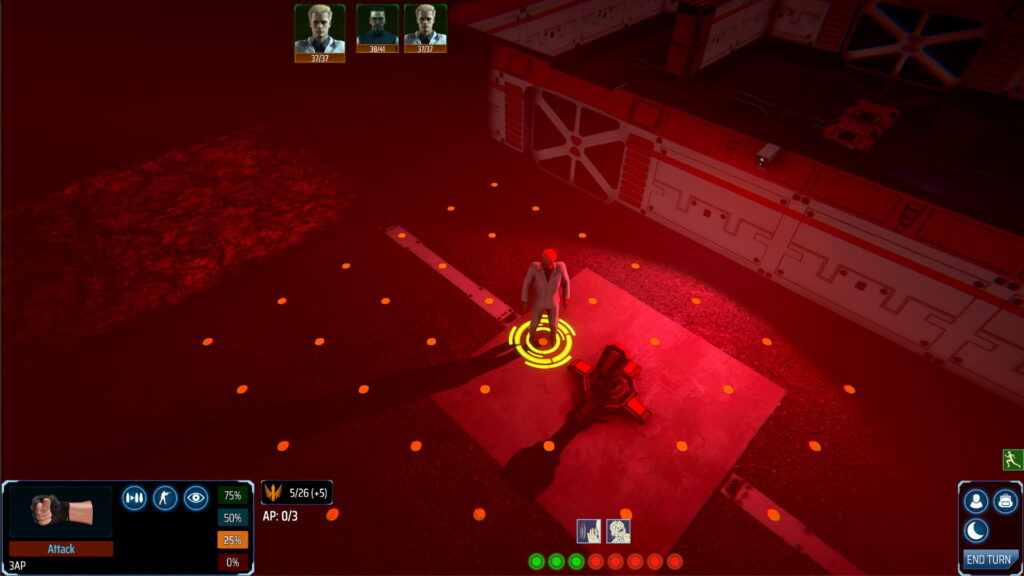
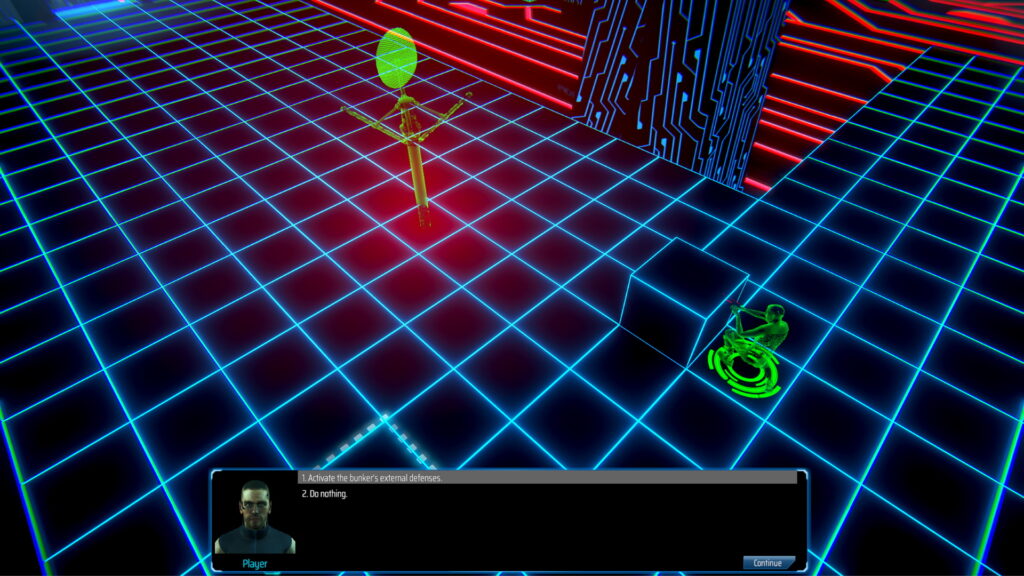

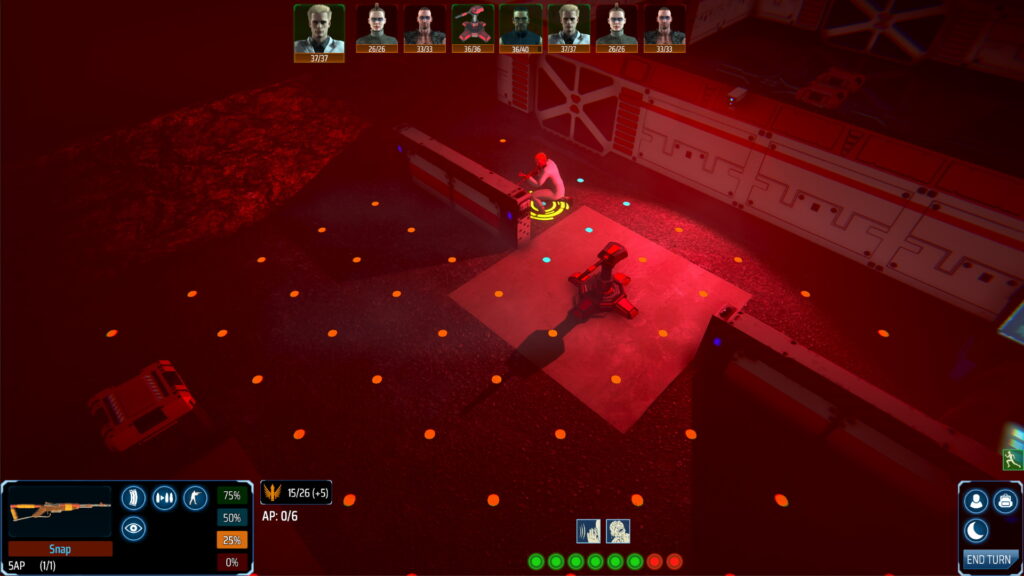
There are multiple ways to handle this encounter: exit cyberspace immediately and fight, try to activate the exterior defences before the marauders reach you, or open the door and try to use the hostile-to-all internal turrets to your advantage.
The intention is to allow players to upgrade and create scripts using the computer science skill and to customise their script selection within the limits of the RAM on their data warfare suite. I’ll follow up in the not too distant future with a video of this encounter and some more screenshots of in-game locations.
If you have any feedback or questions, it would be great to hear from you!
Take care,
Daithi



Leave a reply